In the following image you can see several important technical details of Access Control Methods in the area of Cybersecurity:
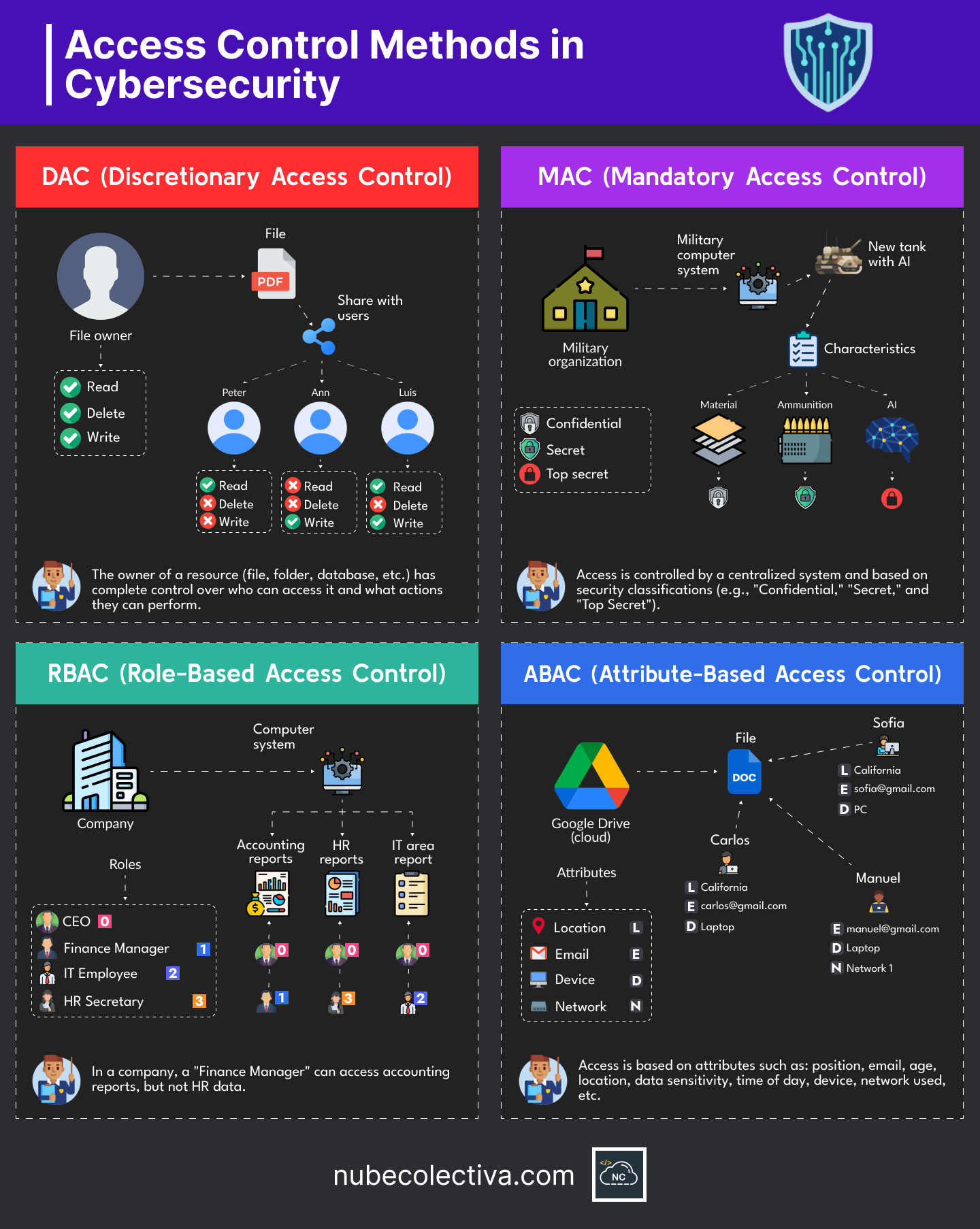
In the following image you can see several important technical details of Access Control Methods in the area of Cybersecurity:
